Category: Tech
Google Assistant and Bixby are two of the most popular virtual assistants in the world. Both of these virtual assistants have their own advantages and disadvantages. However, to understand the advantages and disadvantages of both...
In terms of electricity connection, Delta and Wye are two of the most important electrical connection systems in the world. The Delta system is a three-phase, four wire system while the Wye system is a...
Nano and micro sim are two different types of sim cards. Both are used to store data, but there are some differences between the two. For example, a nano sim is small in size, while...
As a species, we have used candles and oil lamps for centuries, but with the introduction of electricity in the late 19th century, people began to experiment with electric lighting. There were many different approaches...
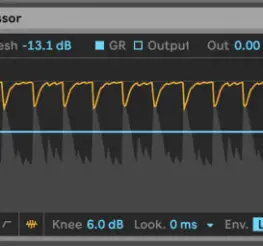
A compressor and a limiter are critical components of audio production, but while they function quite similarly, they are far from being interchangeable. Read more to learn about the differences between the two. Summary Table...
It’s a common misconception that the Internet and the World Wide Web are two synonymous terms. Although these are different concepts, both are pretty closely tied to each other. Summary Table Internet World Wide Web...
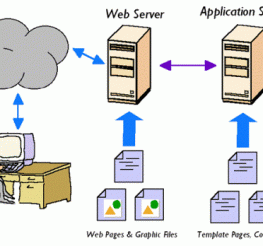
In this article, we’ll find out about how a web server is different from an application server. Summary Table Web Server Application Server Normally stores webpages Usually stores applications Mainly handles HTTP requests for webpages...
Often we hear the words picture, photo and image used interchangeably, yet they somehow still sound correct. It’s not really that big of a deal, but for the sake of their existence, why not use...
Believe it or not, most people have little to no idea about the difference between a web browser and a search engine. If you do know the difference, congratulations, but for the others who don’t,...
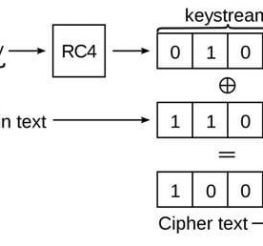
With wireless networks, or Wi-Fi, becoming the norm in most homes, it has become a target for many hackers and key-loggers due to poor security network. This is why WEP, WPA and WPA2 were created....