With wireless networks, or Wi-Fi, becoming the norm in most homes, it has become a target for many hackers and key-loggers due to poor security network. This is why WEP, WPA and WPA2 were created. So what do they do and what are their differences?
Summary Table
| WEP | WPA | WPA2 |
| Uses RC4 (Encryption) | Uses RC4 with TKIP | Uses AES and CCMP |
| Reduced data speed (30%+) | Reduced data speed (30%+) | Slightly reduced data speed |
| Least secure | Less secure | More secure |
| Emerged in 1997 | Emerged in 2003 | Emerged in 2004 |
Definitions
WEP
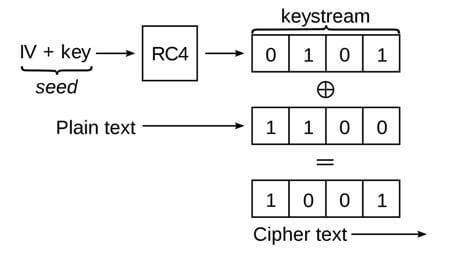
Also known as Wired Equivalent Privacy, WEP was part of the original 802.11 (Wireless Local Area Network) standard in 1997. It is a security algorithm meant to provide data confidentiality similar to that of a wired local network, hence its name. WEP uses RC4 (Rivest Cipher 4), a stream cipher algorithm that is intended to encrypt data. It was the most often used security measure at one time, and it is the default security choice presented by most routers in their configurations. WEP was even ratified as the Wi-Fi security standard in 1999. In 2004, however, WEP was finally deprecated due to numerous security flaws. This includes a restriction of only 64-bit encryption (lifted) and easy-to-crack passwords.
WPA
Also known as Wi-Fi Protected Access, WPA is a security protocol and security certification program that is supposed to an answer to WEP’s major weaknesses found by researchers. It became available in 2003, just a year before WEP was deprecated.
Said to be the answer to the major vulnerabilities of the WEP standard, WPA includes the Temporal Key Integrity Protocol (TKIP) to increase cryptographic strength from RC4, and it also includes message integrity checks to determine if packets passed through the network have been altered. Despite all of the improvements, public demonstrations still show that WPA is vulnerable to intrusion. While it is said to be better than the previous security protocol (WEP), WPA was only an intermediate measure while waiting for a more secure and more complex wireless network security, the WPA2.
WPA2
Also known as Wi-Fi Protected Access 2, WPA2 is also a security protocol and was the intended replacement for WPA. Certification started in September 2004. Unlike in WEP and WPA, AES (Advanced Encryption Standard) algorithms were implemented. Aside from that, CCMP (Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) was also introduced as a replacement to TKIP (still available in WPA2 as a fallback).
With these significant changes, cyber-attacks are easier to deflect since attackers need to be inside the Wi-Fi network in order to access other devices in the network. This means it’s as secure as it can be, especially for home networks.
As with WPA, unfortunately, a vulnerability of WPA2 is through the Wi-Fi Protected Setup (WPS). While it does take at least 2 to 14 hours for an attacker to get inside your network system, not to mention the hard work put into it, there is still a major security concern. One way to counter this vulnerability would be disabling your WPS.
WEP vs WPA vs WPA2
To fully understand the differences between WEP, WPA and WPA2, one should know how network security works. It starts when you are sending or receiving data from one end to another through Wi-Fi. The data being transmitted will then be converted into a radio signal. You must understand that these signals can easily be captured with common gadgets, and unless the data is encrypted, it can be read by whoever is eavesdropping on your network. This is where WEP, WPA and WPA2 come in. They encrypt your data to conceal it or protect it from eavesdroppers.
Now starting with each one’s security strength, there is no doubt that WPA2 is the most secure one. In spite of WEP’s capability to encrypt data, the first characters of its output are not random. This means that if you get enough packets from the transmission, you can easily uncover the WEP key. WPA does seem to be more secure, but since it was just a short-term workaround, more weaknesses were exposed, so WPA2 was developed.
Depending on which security measures you are using, you might not get the full potential of your local network’s data transfer rate. In a performance test done by Tony Fortunato, a senior network performance specialist, WEP’s maximum transfer rate was four times lower than of that of WPA2-AES. As with WEP, WPA reduces the processing power of the network device. In addition, depending on your router, performance can slow down by 30 percent or more when enabling WEP or WPA. WPA2 is more secure than the other two and is much more efficient in terms of performance.
In summary, WPA2 is a superior security protocol to WPA, which is in turn a superior security to WEP – not only in securing your data, but also with data transfer rate. Take note, however: depending on your hardware, WPA2 can also reduce performance if outdated.